Today I did a fun POC on KeyCloak and Active Directory, and I justed wanted to share my findings. In my case KeyCloak is used by a corporate system on top, in which we want to use our AAD users for login and role assignment and so on.
The KeyCloak Server
For this POC I followed the excellent documentation on https://www.keycloak.org/docs/latest/getting_started/index.html to set up my local KeyCloak Server. Once up and running go to http://localhost:8080/auth to create your admin user.
Configure Microsoft as Identity Provider
Before doing anything else in KeyCloak, go to portal.azure.com to create an App Registration for KeyCloak. This App is basically the key used by KeyCloak to authenticate your AAD users with your Azure Tenant.
NB!! – You need administrative permissions on Azure to complete these steps
Go to https://portal.azure.com. Find and create a new application registration.
Give your Application a name, and state who will be using the application? In my case, KeyCloak should only be able to authenticate AAD users within my own tenant, so I select Single-tenant. You may need to select Multi-Tenant if you are authenticating from different domains.
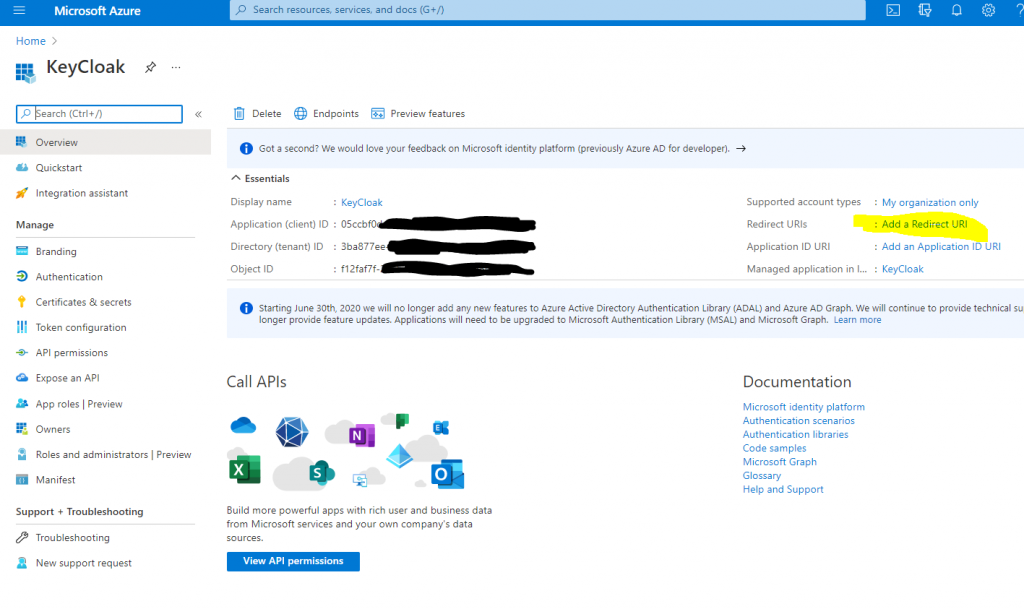
Now on your newly created Azure Application Registration overview, find and note your Application (client) ID.
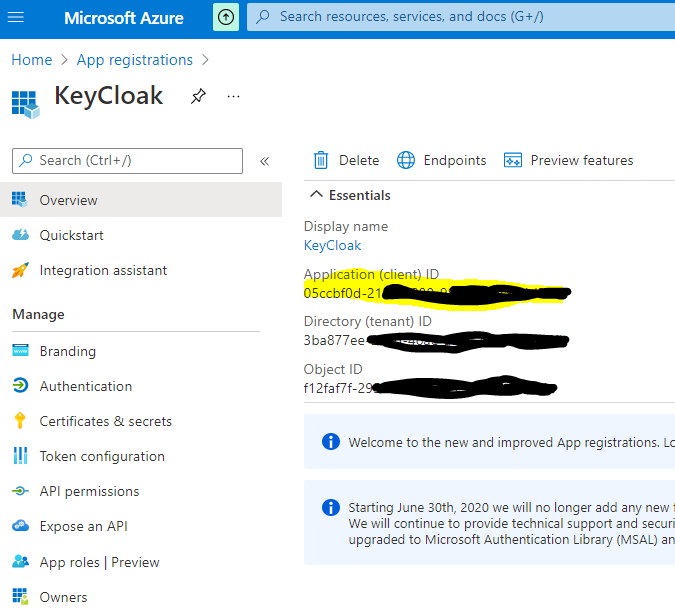
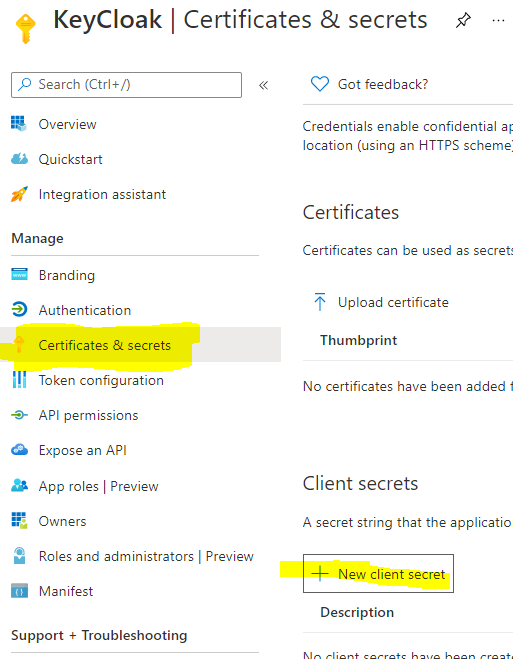
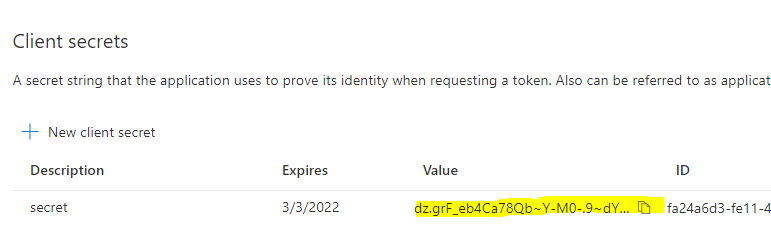
Next, go to your App Registrations’ Certificates & secrets to create a New client secret. Copy the value of your secret to your notebook so we have it for later use.
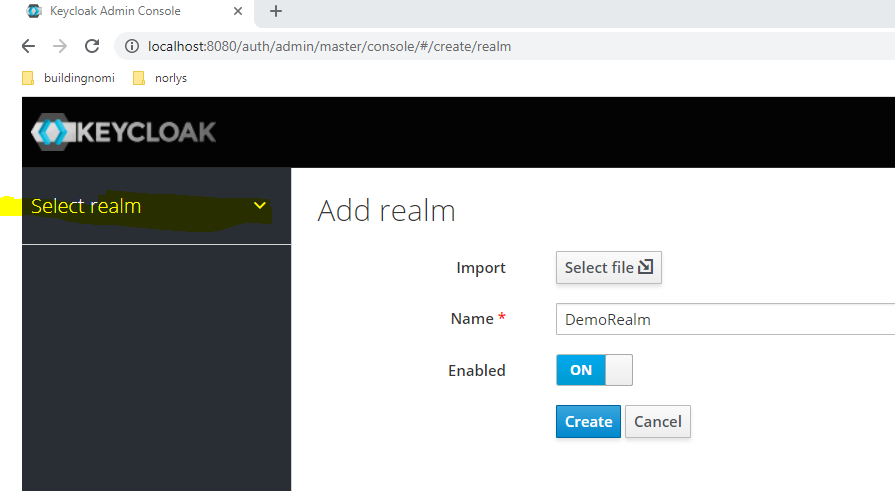
Now back to Key Cloak, login with your admin account, and create a new Realm.
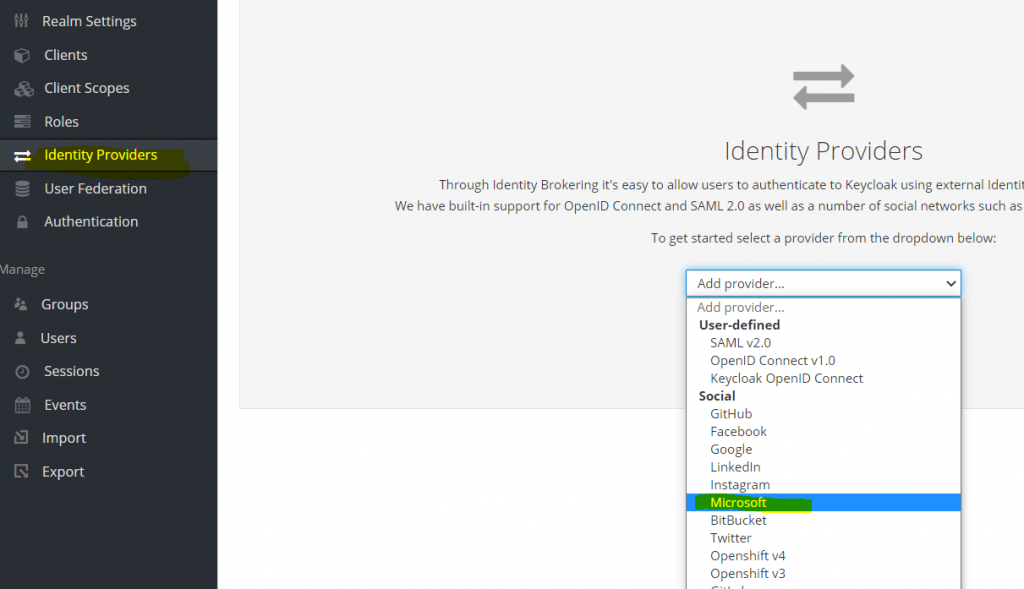
In your new Realm, go to Identity Providers, and add Microsoft as new identity provider.
Now add the Client ID and Client Secret from the App Registration and click save.
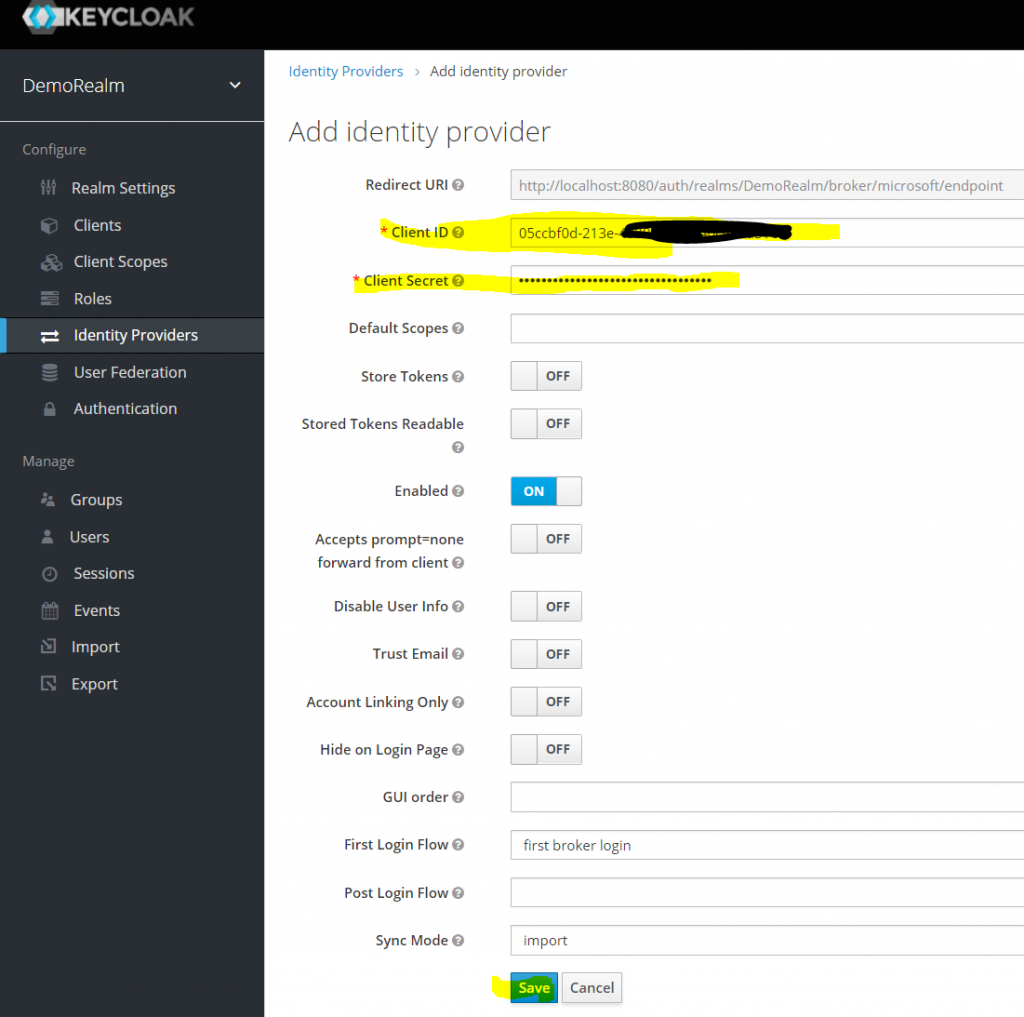
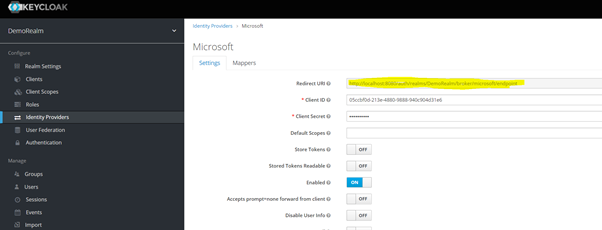
Now finally you need to copy the Redirect URI path from Key Cloak, and paste it into your Azure Application Registration as the Redirect URI.
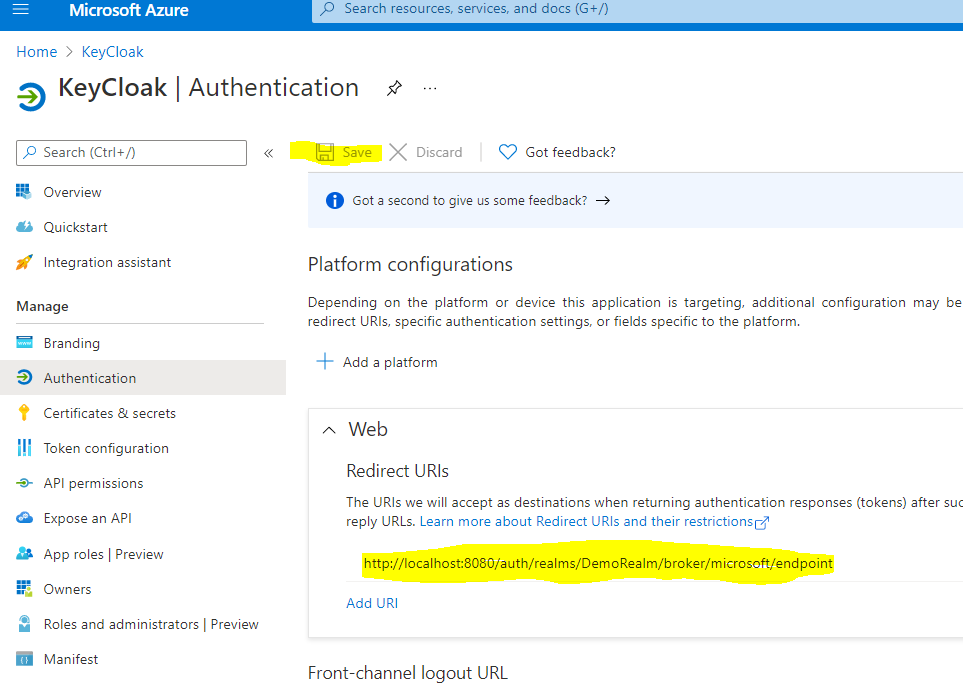
To test you can use the KeyCloak admin console to test login with your AAD account. Go to Clients to find your login URL. (Open this incognito mode recommended since your admin login is most likely cached.)
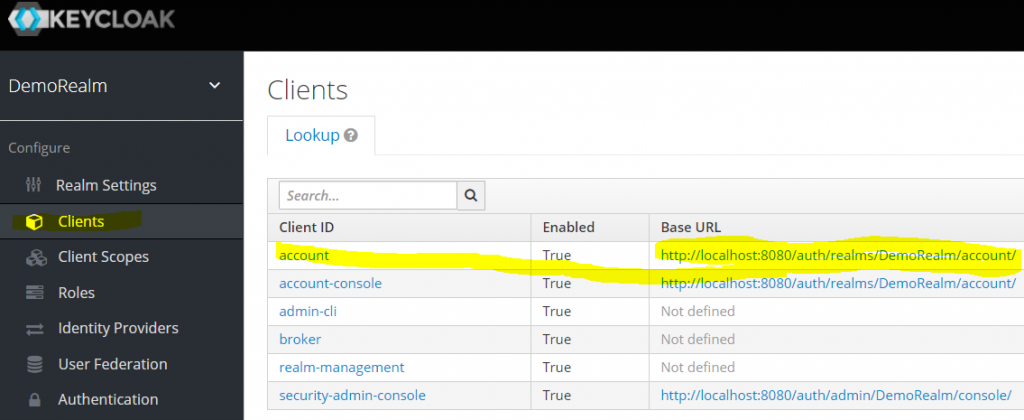
Hit the sign-in botton.
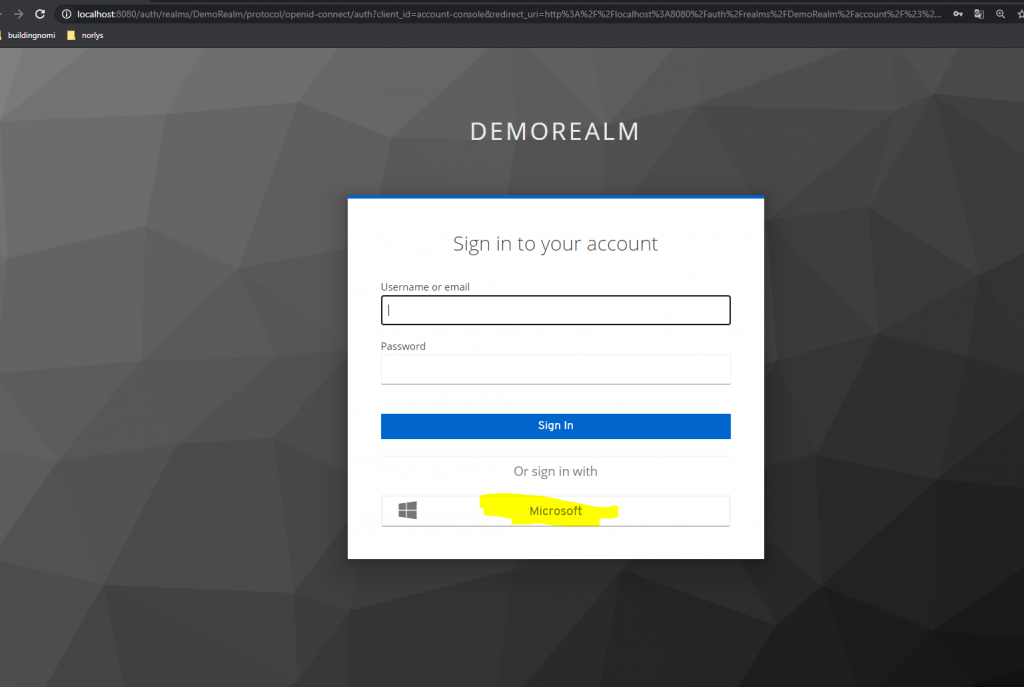
You should now see Microsoft as an login option:
In case you require from the User to login only with Microsoft, you can go to Authentication tab in KeyCloak and setup Required Identity Provider Redirector. And then click into Actions->config on the far right.
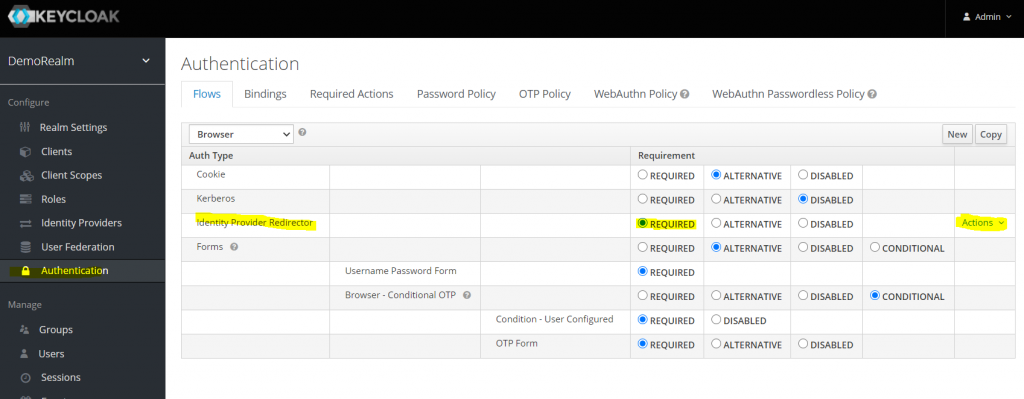
In the configuration you need to type the name of your Identity Provider, it shouild be microsoft.
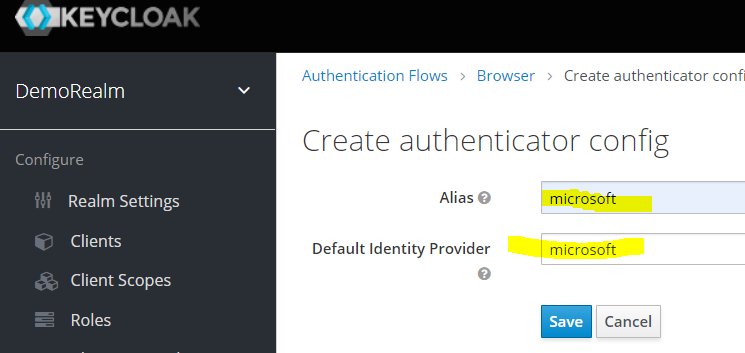
Thats it now you are ready to login using Microsoft as your Identity Provider.
